Banks, Adrian CPT 304 Week 5 OS Theory Concept Map
Describe features of contemporary operating systems and their structures.
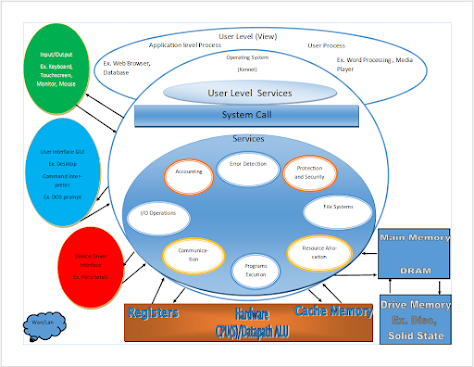
Modern operating systems handle many different processes and procedures. It manages any inputs or output via I/O devices like keyboard, mice, hard drives, network connections, and monitors. It facilitates the communication of all these devices, so they work with each other to create a smooth user experience. An OS provides resource allocation, which not only allows the hardware to work together but as effectively as possible to get the best performance possible. The OS also includes file systems to organize and control your information and how it is saved. The operating system also provides the user with a secure basis for all these interactions to take place. This means built-in security at the language level and tools like domain security to keep all the user's info safe and where they want it.
Discuss
how operating systems enable processes to share and exchange information.
First, the OS will
recognize that it has a process. Once it identifies the process, it will
communicate with the memory and allocate the process, using the RAM and
mechanical hard drives. It will run these commands and processes through the
CPU through single and multi-thread processes. It will then take all the
information it has processed and display it to the monitor in whatever GUI the
user is using. This exchange doesn't happen randomly and without layers of
security. The OS will determine which information or variables can be safely
exchanged between programs and I/O devices without any user security breaches.
Explain
how main memory and virtual memory can solve memory management issues.
Virtual memory is
an abstract storage device. It does not exist physically; the Main memory is your
physical memory unit: your hard drives, your RAM, and your CPU. Your virtual
memory helps with memory management by helping understand how much memory a
said process will need, helping the computer anticipate the workload, and
handling the workload effectively. First, the virtual memory will allocate the
amount of needed memory, then using a memory mapping unit it will move through
all the previously mentioned memory units and allocate all the resources
needed. This makes sure that the processes are being handled with the
appropriate resources and helps keep the system from using either too little or
too much power.
Modern operating
systems use kernels to manage files, storage, and I/O operations. Kernels can
use different data structures to keep track of these processes. Kernels will
handle these processes through I/O ports like USB and Ethernet ports and use
I/O busses to communicate the processes from the devices to the system. There
are different algorithms to how these processes are handled.
First
come, first served is as the name sounds. It simply takes the commands as they
come in the same order. This is the fairest method but can lead to longer
execution time as it requires the driver's arm to move back and forth between
partitions in the drive. Next is the shortest seek time first, which means the
least arm movement in the drive will happen first and continue from there. Again,
this algorithm saves some time on execution as it travels the least between
partitions but can lead to starvation of specific processes if the seek time is
a bit further from the current processes at hand. Next, you have SCAN, which
means the arm will move from its current position to the next partition and
then continue in that same direction till it hits the end of the disk, then
continue the other way and complete the processes.
There are two
types of controlling access to computer systems. Physical, which is how you
secure the physical assets of the systems, like controlling access to where the
systems are stored and securing the systems in place so they aren't taken. The
second is logical. This is done through the system and defines who can access
what. A system administrator usually decides this. The system admin can set up
a domain for each user, which means; the user can only access the files they're
allowed to and not anything else in the system. This allows users to access
only the information they need without affecting other files and minimizing the
damage done if security is compromised for whatever reason.
I will use all these concepts to showcase a more in-depth
knowledge of how an operating system works and manipulate different features
and functions to work how I intend them. I am looking to become a Cyber and
Network Security Manager (ISSM); these concepts will significantly help my
foundation for my future career. With knowledge of single and multi-threaded
processes, I will know how to apply specific coding techniques to create
effective programs—knowing how file systems and domain security work, I can set
up an office environment and manage user access and resources. Along with
corporate and personal security and protection of information and systems and
even equipment.










Comments
Post a Comment